
As UXers, we design with users’ needs in mind (User centered design), we think from our end-users’ perspectives, and we always do our best to design the most intuitive and user-friendly products. But when it comes to simplicity and UX vs. Security and privacy, where do we draw the line? how can we balance between the two? Is it even possible to design secured products without affecting the user-experience?
A bad experience
I just came back home, and then I realized that my Android phone is lost! So I pulled my Macbook out of my bag to find my phone with Google’s Android Device Manager. But the problem was that yesterday at work, I had to clear browser data (Front-end, Cookies and HTML+CSS reasons) and because of that, I was logged-out of my Google account!
And yes, like most people, my account is secured with Two-Factor-Authontication, and without my phone, I was locked out of my own account, and couldn’t even find my phone! That’s a bit annoying because in that exact moment, all you care about is finding your phone as quick as possible. No matter what you do, without your phone and your two step authentication code, it is impossible to access your account! it’s the “chicken or the egg” paradox…
Security is important
Well, by now you probably use Two-Factor-Authontication (2fa is turning your phone into an authentication device) for your online accounts, and if you don’t, you should use 2FA! It is highly recommended to use an extra layer of protection, because today more than ever, it’s so easy for anyone (amateur hackers and even bored teenagers!) to hack online accounts. There are so many creative ways to access your cloud accounts, from Social-Engineering, Phishing and even simple design manipulations (and even UX-Dark-Patterns). So yes, today even people without hacking skills can learn how to hack, from online tutorials and YouTube videos.
Balance between UX & Security
So let’s focus on Two Factor Authentication, and see how Apple and Google are dealing with it. Imagine that you just lost your Phone and you’re in a rush to find it! time is against you now! so if you have an iPhone you’ll go to Apple’s Find my iPhone website to find your phone. And if you have an Android phone, you’ll go to Android Device Manager website to find your phone.
But since your account has a Two Factor Authentication, you can’t prove that you are who you claim you are without your phone! So what are you going to do? Well, this is a classic example, because we know that Google is more Security focused than Apple, and it’s a good thing, but we also know that Apple always was obsessed with design, experience and simplicity. So even in this case, it looks like Apple solved a security issue by design, even better than Google! let’s take a deeper look, analyze and learn from it.
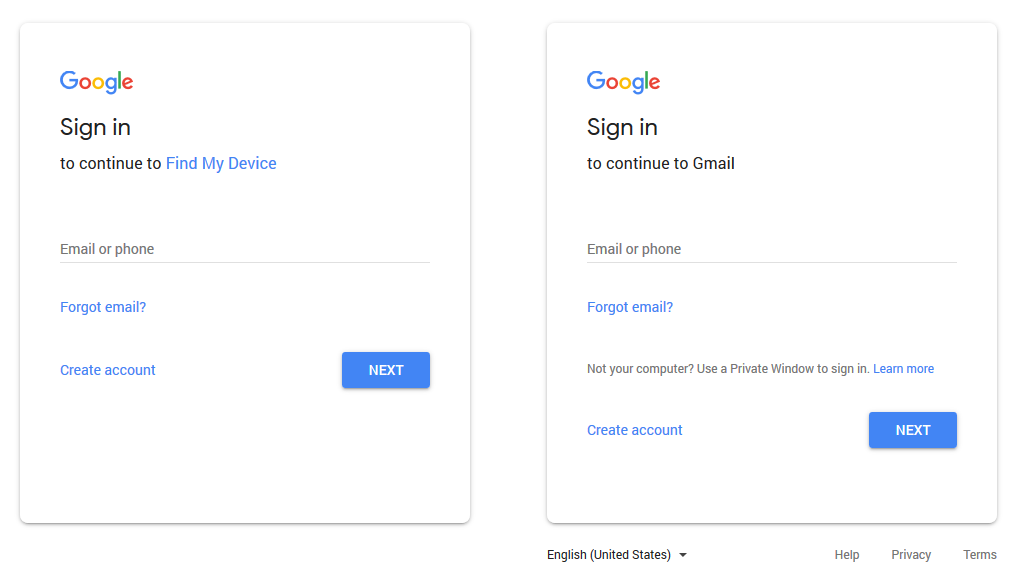
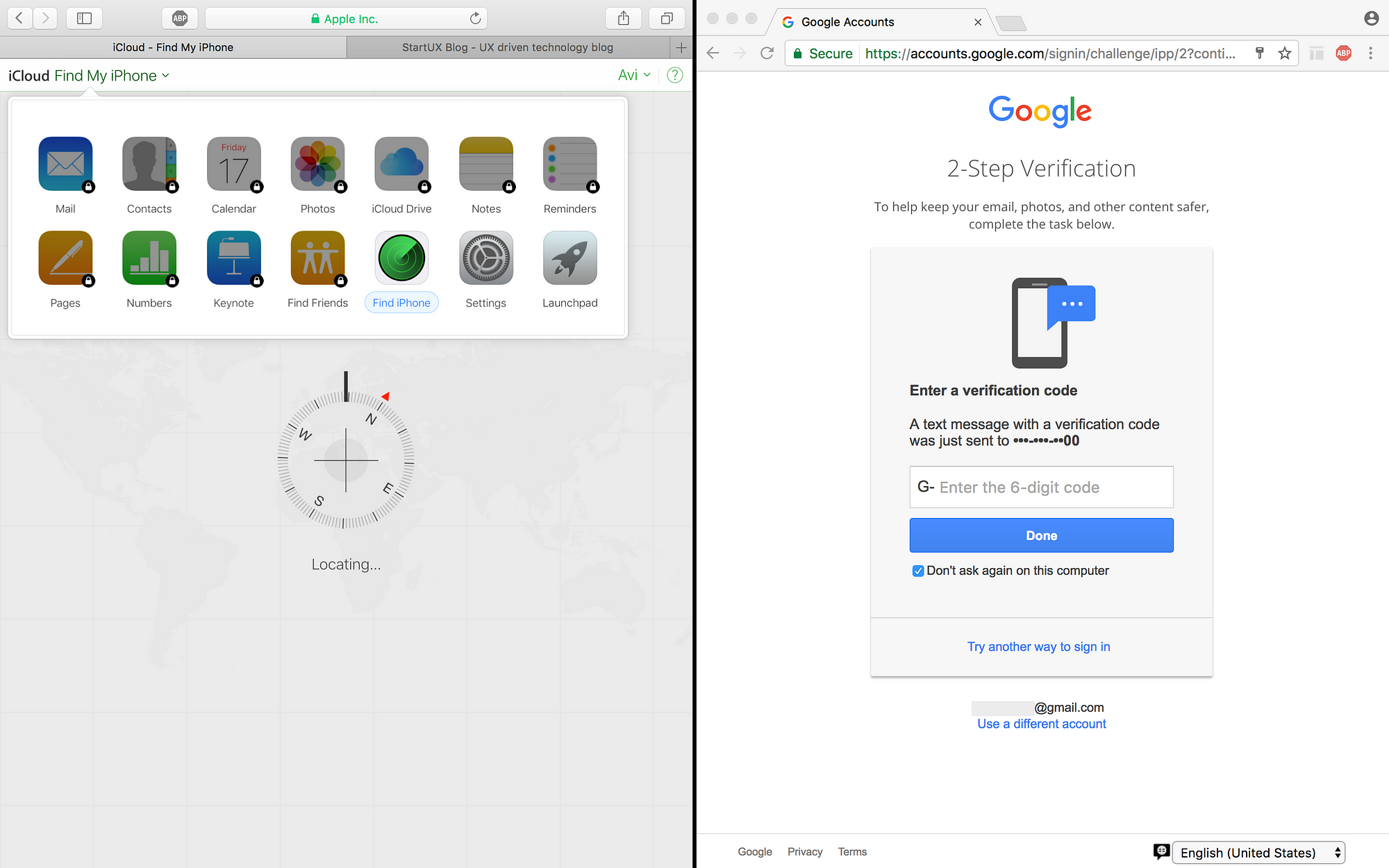
1. Sign-in experience
iCloud is simple, but Google has different sign-in UX with its pros and cons. (By the way, showing users’ picture is nice, but hackers can verify that this account belongs to you).
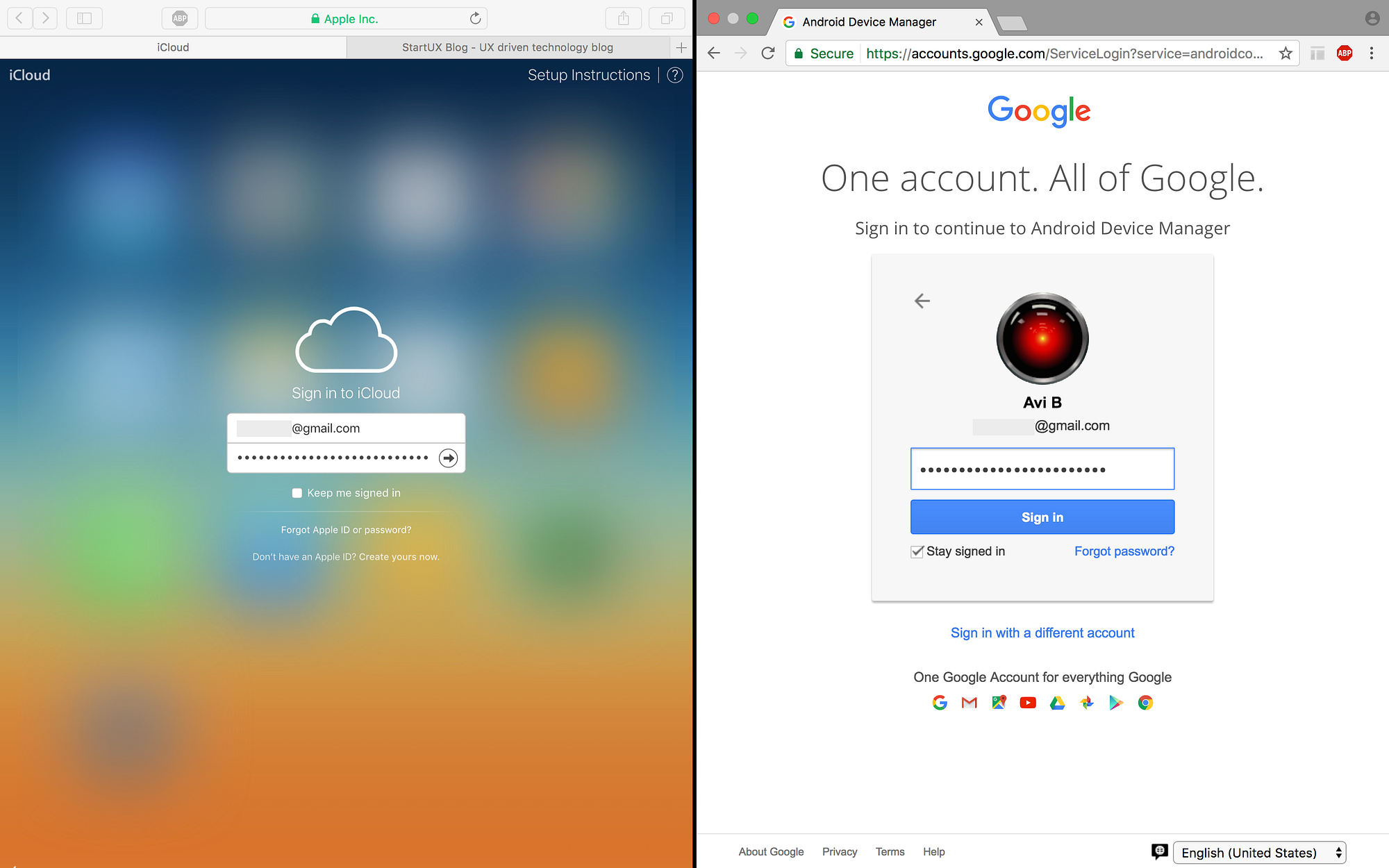
2. Two-step-authentication
Apple lets you in, while Google wants you to authenticate with your phone, but the only problem is that your phone is lost!
3. Locating my iPhone…
Apple helps you to find your iPhone, without forcing you to authenticate! because they know your time is valuable and you are in a rush. While Google wants you to work harder…
4. Mission complete, iPhone found!
Just to be clear — Apple only lets you access the “Find my iPhone” page, and you won’t be able to access other sections in your iCloud account! But it’s a good thing, because if someone hacks into your account, he’ll be isolated from your data, and thanks to 2FA you’ll get a notification to your iPhone / Mac that someone used your Apple ID to accessed you account. and even if your iPhone is gone for ever, you’ll still be able to access your iCloud data.
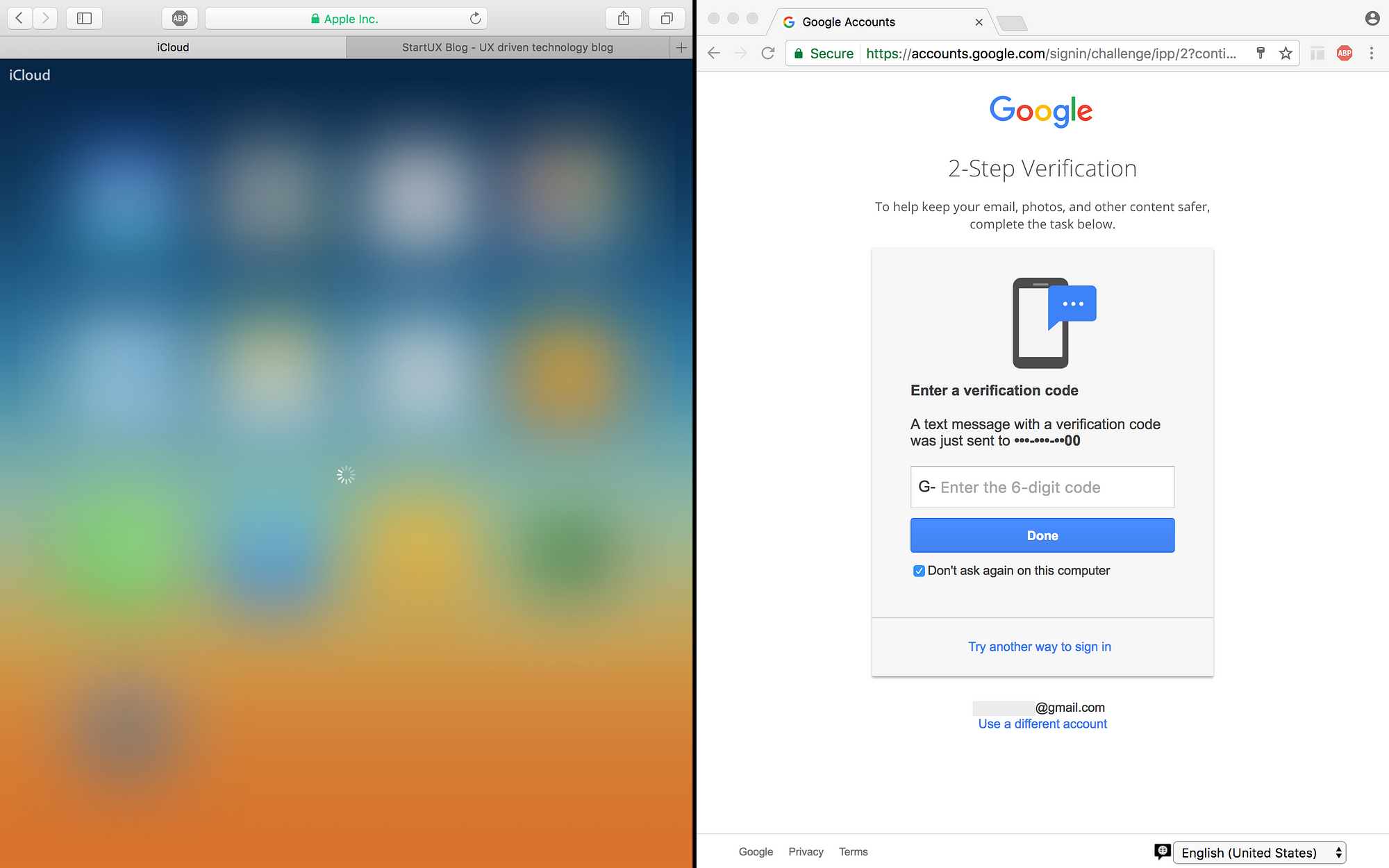
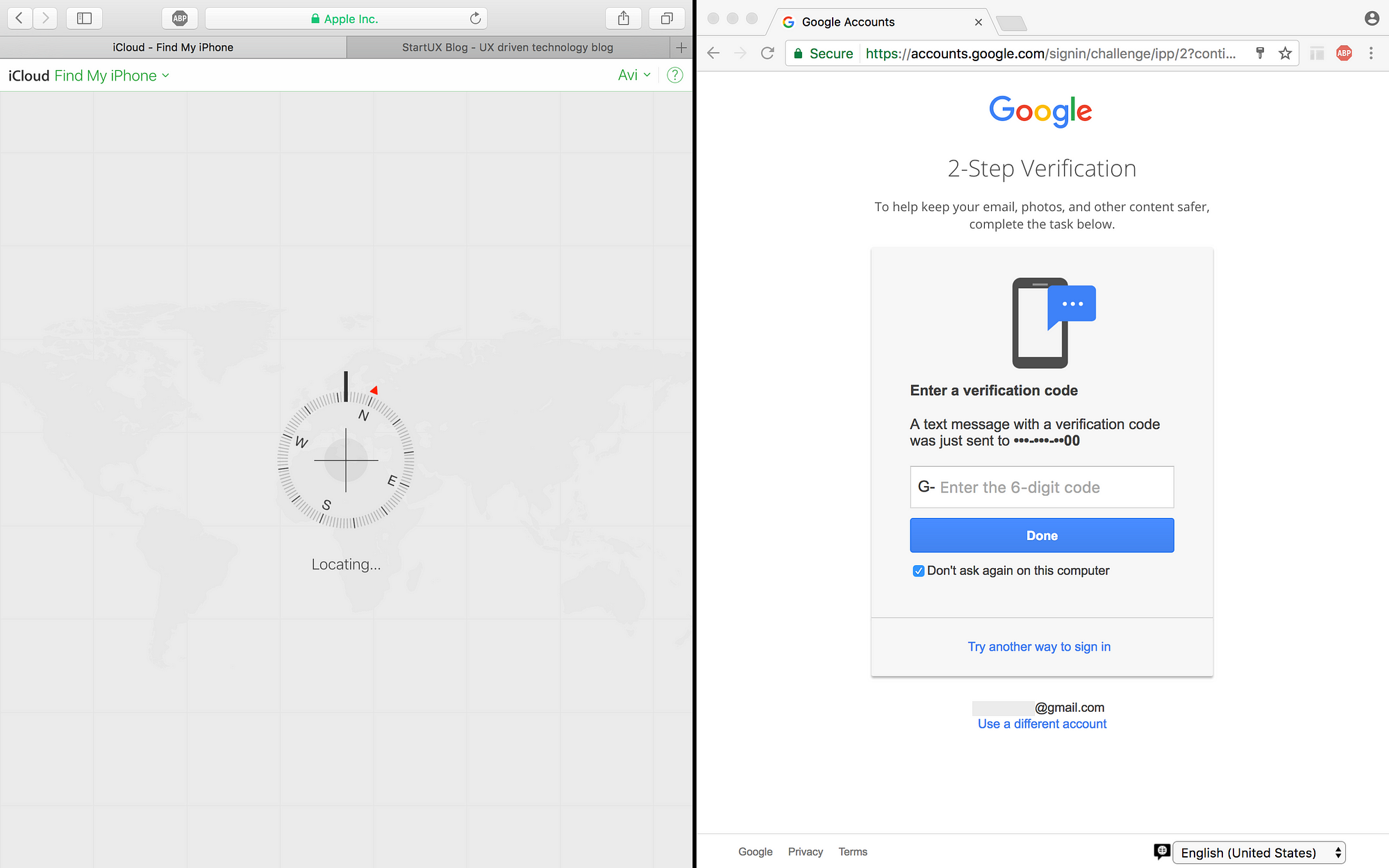
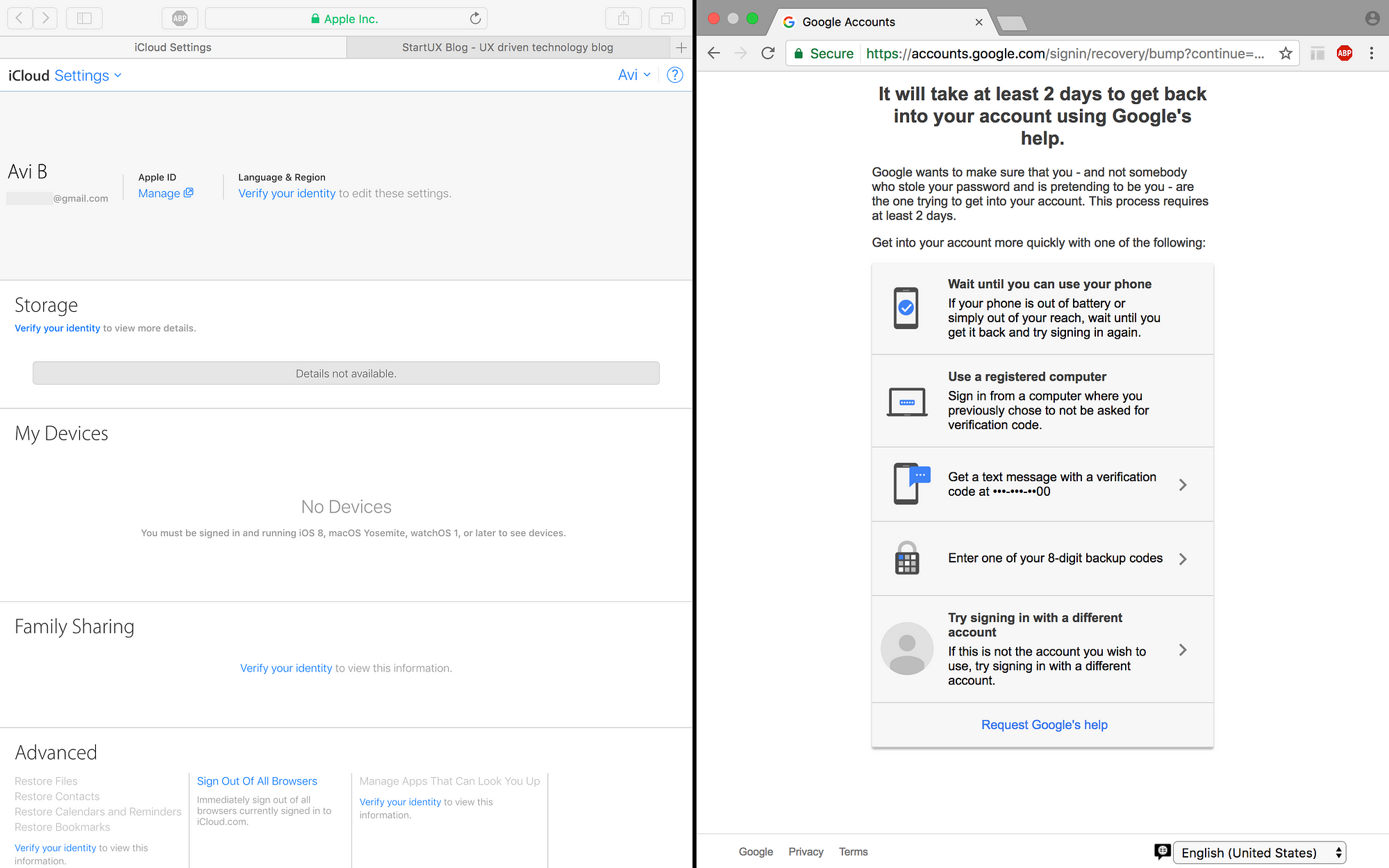
5. But Launchpad wants 2FA
Launchpad wants your authentication! so if someone hacked into your account, he is isolated in one place. So in my opinion, there is no doubt – Apple did a better job both in terms of UX and Security! Because even without authentication, you can at least locate your phone!
6. You shall not pass!
So without authentication, Just like Google, even Apple won’t show you any personal data on Settings page. As for Google, well you are still locked out of your account, without a way to locate your Android phone. Google — please fix it 🙂
7. Be calm and prepare yourself!
Unless you have a registered computer nearby, you are locked out of your Google account! so prepare yourself, make sure you have backup codes! you can store them on your computer, a thumb-drive, or even other cloud accounts such as DropBox, OneDrive etc. (make sure you encrypt / password protect your codes). Be prepared! otherwise you’ll have to deal with this:
In summary:
Even today, Apple is more design oriented when it comes to balancing between security and usability, but until Google will do something about Android Device Manager, make sure you are prepared, otherwise you’ll waste valuable time before you’ll find a way to access your account (if ever) without a registered phone. So don’t be lazy, take Google’s advice and get your 8-digit codes right after you activate Two Step Authentication. Just in case you lose your phone, at least you’ll be able to access your Google accounts.
So, the good news is that you can do something about it, and there are several ways to make sure you never get locked out of your account in case your phone was lost or stolen. In fact, Google even suggests you to do something about it right after you enabled Two Steps Authentication, but I guess most people ignore it. So it is your responsibility to do something about it and be prepared! otherwise Google will not help you!
By the way, Luckily for me, I already had a backup for my 8-digit codes on my computer, So eventually I was able to find my phone… It was in my car! it probably fell out of my pocket. But this (terrible) experience made me realize that we should be prepared, and I wanted to share it with you, just in case you’ll lost your phone…
P.S. Please feel free to comment and let me know if there are any other workarounds / hacks / official documentations, for people who locked out their accounts.
Update (Jul 22, 2018):
This article was originally posted at StartUX on March 16, 2017, but I wanted to re-publish it on Medium, so I checked if something has changed since then, but except some design changes on Google’s side (They’ve applied Material Design to their Login screens), but other than that, nothing has really changed:


Leave a Reply