
Lately, there have been many articles published about Design and UX in the context of today’s hottest topics, such as Cybersecurity and Privacy. However, what’s really special about these articles is the unique approach to these issues, from a design perspective, by encouraging user-experience designers with a holistic point of view, to take part in the early stages of product design. And also to participate in the problem-solving process by applying innovative design thinking methodologies, and encouraging design driven-innovation in a variety of fields, even outside their comfort zone. Given that nowadays, most of the designers care about a lot of issues in the tech world, and they can help in many ways to come up with better solutions. Designers have the power to change the world and improve people’s lives by making products and tools that give them magical experiences. So why not apply it everywhere?
“Best way to change the future is to design it” – M. Cobanli
Design thinking methodology has been proven to result in more creative solutions in many fields and has been applied successfully in business, strategy and to social issues. But now more than ever, it can help not only in problem-solving but also in user-centered design and personalized product planning, in order to make things as simple as possible for the users. Let’s take cybersecurity for example: keep it in the back of your mind and approach your design with the assumption that your user has zero knowledge in security and privacy, so the key is, to build better, intuitive, and easy to use products, even for the average user, so they will be able to sleep in peace at night, knowing that they are protected thanks to your product.
After all, unlike the president of the United States, nobody takes care of your security and privacy issues. And if that’s not enough, even Donald Trump is not immune from hackers and foreign espionage, because as it turns out, Trump is still using his unsecured Android phone to tweet. As you may know, the president’s official phone is secured by the white house security experts, and he can’t install third-party applications at all.
Why we need design thinking in Tech and Innovation?
We are living in interesting times; technology has really changed and improved our lives in the past ten years. Thanks to our smartphones we are always connected to the internet, and we have information at our fingertips, 24/7 from anywhere and anytime. And today more than ever before, we are always online, available, and even addicted to wonderful and intuitive user-experiences, we enjoy using our smartphones for a variety of internet based content, applications, and cloud services. So the internet is becoming an extension of our mind, not only because of Crowdsourced information but because it enhances our experiences, knowledge and human capabilities in general (well, at least until we are all cyborgs – The singularity is near).
But as always, technology is a double-edged sword! Just like it enhances our lives, it also exposes us to increasingly dangerous threats. Because we are always connected, we consume more and more internet services, content and applications, so the average user is now even more vulnerable than President Trump, not because of professional hackers or foreign organizations, but because we are exposed to any application developer and even to amateur hackers.
So your smartphone is always on you, and it becomes the ultimate spy tool because any application you have installed from the app-store can spy on you. Any “innocent” app that has questionable permissions can access your microphone, camera, gallery, contacts, storage, documents, email accounts, bank accounts, etc. And they can even “phone home” to send it all back to the developer’s (and even to a small or large organization) servers without you ever knowing about it!
And even if you don’t care about privacy, what about your professional life and work environment? You are exposed even when you walk around in your office. Industrial espionage has become easier than ever, because if spy apps can access your phone’s microphone and camera, then you are in danger! Imagine that every confidential business meeting, every financial discussion or even a top-secret project meeting is exposed.
How can design thinking help?
Well, It’s true that most of the people ignore security and privacy issues, as long as they get wonderful user experiences from their device, applications, and services. Let’s face it, we all use internet services (email, cloud services, and social networks) especially when it’s “for free.” But it’s very important to let the users know about data collection, and of course give them more controls over their data and privacy settings, with an easy-to-use mechanism, particularly for the average user who has no understanding of technical stuff like permission management, firewalls, and other security tools.
Apple has been doing that for years; iOS always informed users about privacy in a simple way. But in Android, on the other hand, there were many security and privacy issues over the years. Users will likely never receive system updates from manufacturers, there is no firewall even in the original Android Open Source Project (AOSP), and of course, a lack of decent permission manager! It took Google many years until they released a permission manager in Android Marshmallow 6.0 (Good job Google! It’s even better than iOS), but it’s not perfect yet, because most of the users are still ignoring warning messages about security and privacy issues, and they are still exposed! So there’s gotta be a better and smarter solution to all of this…
Android is an amazing OS which I really like, and now it’s even Desktop optimized (supports X86 hardware), and the funny thing is that compared to other Operating systems, especially Linux flavors (Android is based on the Linux kernel) Android doesn’t even come with a basic firewall out of the box! As I mentioned before, it took them forever to include a decent Permission Manager in Android, while alternative Android open-sourced flavors (CyanogenMod, ParanoidAndroid, AOKP, etc.) came with powerful permission managers and Root privileges out of the box, and if that’s not enough, Rooted Android ROMs are easier to manage for power-users, and even installing a firewall is a simple task, so users are able to blacklist all applications (Outbound & Inbound traffic) and services except few apps they really trust.
Just to be clear – I’m not talking about “classic” firewalls and complexed IPtables, and although I really like the simplified and great firewalls in Windows and macOS, and when it comes to user-friendly firewalls, the best one I’ve ever used is Little Snitch (Macs only). If you want a firewall that will allow you to choose which apps get to connect to the Internet or not, go and try it! I couldn’t find anything like that even for Linux (and you don’t really need that on Linux). And as for windows, I prefer Eset Smart Security’s firewall (Interactive mode only!), but for simplified mobile UX – we have to think out of the box.
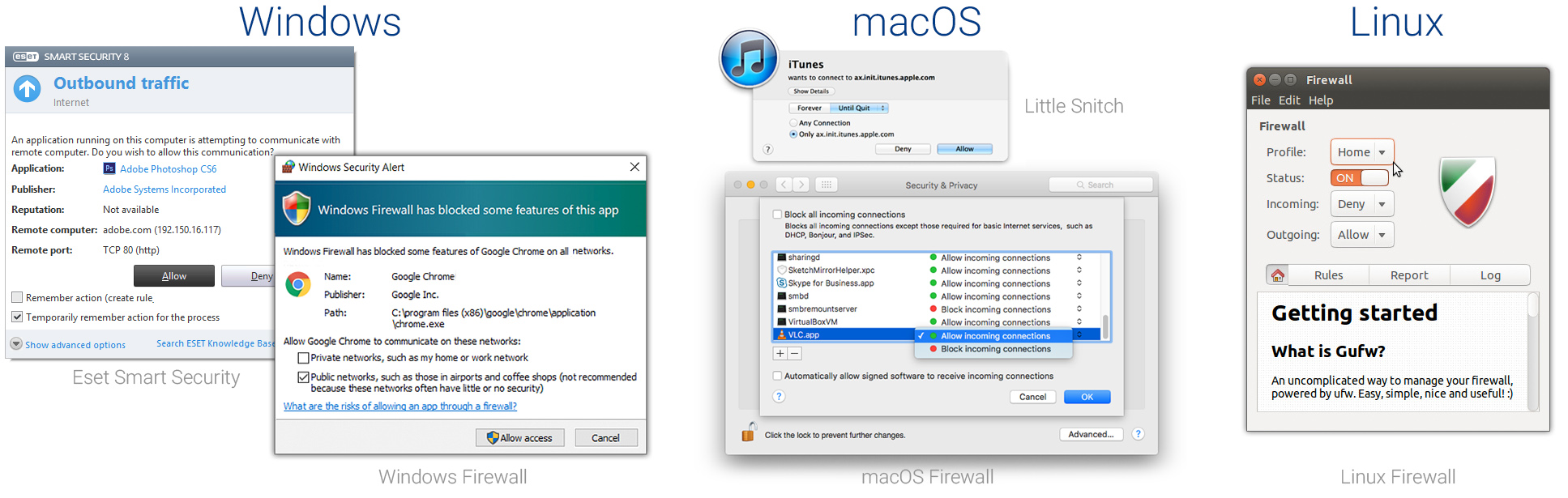
What can be achieved by design thinking?
I had to try it myself, so I’ve decided to take up the challenge and do something about it over the last couple of weekends, a little side project to solve this problem, inspired by an idea that I had a few years ago when I moved from iPhone to Android. Well, personally I just love technology, I’m a tech enthusiast, an entrepreneur and a geek who is always passionate about technology, so if I see a problem, I want to solve it. And after a short planning, sketches and short brainstorming, I have developed a quick prototype (MVP) that aims to solve the problems I’ve mentioned, but more than that, simplifies everything for the average user, in order to deliver a magical experience. Simply hit a button and wallah, your problems solved!
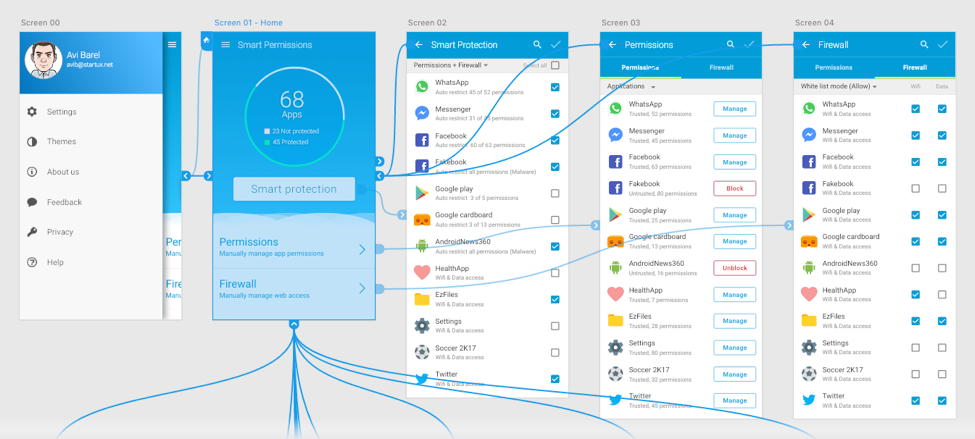
- Discoverability and ease of use – Since we are talking about security and privacy in Android, only those who are aware of Android’s permissions manager, are those who actually use it. And only if they really have the desire to make an effort to protect themselves. Since the permission manager in Android is not so discoverable, some users never used it. That’s why it is highly important to make it discoverable, intuitive, and easy to use. It’s the only way to encourage users to use it with no knowledge of Privacy or Cybersecurity. But how you do that? More dialog messages? No! Let’s use Crowdsourcing!
- Smart permissions – Make it easier for everyone (even for non-technical users) to protect their device and privacy, which can be solved very easily, for example by applying smart Crowdsourced policies that were configured by thousands of other users, who choose to share (anonymously) their app permissions to help others. But more importantly, perhaps making the process easier and productive for everyone, especially for non-technical users. Imagine that some users (say 1000 users) blocked camera access for a particular application, their policy will be automatically shared with the crowd, in order to make everyone’s life better. Think about non-technical users, if only they could get this capability today, thousands of people around the world will be able to hit a single button and instantly make their device secured thanks to crowdsourced security configurations. And if that’s not enough, just Imagine that everytime you install a new app, you’ll get a little notification that warns you about questionable permissions in that app, for example: “Hey, 1,000 users have blocked this application from accessing the camera, would you like to do the same?” And even if you have dismissed the message, you can always undo that, just launch smart permission manager, and you’ll get an intuitive, easy-to-use interface with a simple “Smart Protection” button, which you can simply tap, and it will do wonders – it will automatically block any suspicious apps on your device, thanks to the Crowdsourced data. We can even use Machine Learning and AI capabilities in order to improve that process.
- Smart Firewall – A permission manager is not enough, because there are so many apps and games with a full network access (without any logical reason), like that flashlight application which came with so many questionable permissions and also an internet access. Let’s say that there’s only one flashlight app out there that does what you need it to do, but it has so many permissions, and it looks suspicious to you, but you don’t have a choice because that’s the only flashlight app and you really need it… what are you going to do, avoid installing it? Maybe, but what if you had a simple way to prevent this app accessing the Internet? So that way, even if it has access to your valuable data, it won’t be able to send it over to the app developer’s servers! And you’ll be able to use it anyway, knowing that your data is safe. So the point is – we need a firewall combined with a permission manager. Just like Smart Permissions, Users can protect themselves by using a crowdsourced firewall that is capable of recommending which application to block hermetically from accessing the web, in order to prevent outbound data leakage or even inbound traffic and vulnerabilities by hackers. So it’s not only about turning the traditional (and complex) firewall into an user-friendly and “Smart” (crowdsourced) firewall, but it’s about “killing two birds with one stone” by providing Millions of mobile users out there with a simple and easy-to-use firewall, for the first time for mobile devices. As you may know, for years people had to Root their devices in order to install a basic permission managers and firewalls, but no worries, there’s a solution even for unrooted devices – Technically it’s possible to implement a firewall as a service (FWaaS) in a single Smart Permissions app, so even users without rooted Android or Jailbroken iPhones will be able to get a simple permissions manager and even to block internet access for some applications via simplified firewall. And all of that from an intuitive and user-friendly application that enables non-technical users enjoy privacy and protection, thanks to policies and configurations that power-users have shared with the community, in order to help thousands of other users out there to restrict untrusted apps simply by pushing a button.
Demo: How SmartPermissions app works
SmartPermissions will empower you to achieve better security and privacy!
What’s next and how this approach can help
Keep in mind that this article was written before our products were “Smarter,” thanks to the IoT (Internet of things), and it doesn’t matter if we’ll have “smart home” products in every room at home, not to mention “Smart” toys that can ‘spy’ on children or “Smart” autonomous vehicles which we can buy even today (my favorite one is Tesla). Just remember that when we implement computers in vehicles, and “smart” products to connect them to the internet, we’re actually taking all of the security issues we had for years in computers and bringing them to all “Smart” products in our lives, doesn’t matter if it’s inside or outside your home (on wheels). It’s relevant not only for you and your family’s privacy and online security because it has become a real life-threatening reality! Not to mention Smart robots with AI brains that will be controlled from the cloud, if you are scared of hackers taking remote control over your robots, just watch I, Robot or Terminator movies to get some ideas. Sometimes science fiction becomes science fact…
Now seriously folks, it’s very important to adopt an entrepreneurial, and creative state of mind, in order to predict upcoming problems before they occur, and it is important that everyone takes part in these upcoming challenges, doesn’t matter if we are talking about designers, engineers, entrepreneurs and other professionals from other disciplines.
Hence, diversity is good, and it will make an impact because everyone can see a problem from a different perspective, and they can share values, ideas, and skills. Together in a diverse way, we have better chance to solve any upcoming problems. Therefore, it’s very important to start thinking outside the box about those upcoming challenges, and even more importantly, think about problem-solving today! As said – creative design thinking and innovative design strategies should be applied as soon as possible in all technological and business fields, and it is extremely important to remember this even before you approach the next challenge.
In summary:
Why? Because if you care about something, do something about it!
How? By Applying Design Thinking as a framework for Innovation.
What? In this case, better security and privacy tool for everyone.
We’ve got to appreciate the fact that in the recent years, there has been a shift in technology and high-tech industry when it comes to design thinking! Because nowadays you can’t innovate and create disruptive technologies (Products and Services) for humans, without involving product and experience designers as early as possible in the development process – research, planning and concept prototyping (MVPs) because designers are the voice of the user. Design thinking methodology has been applied not only in the start-up ecosystems, but it has been applied successfully also in business and to social issues. So it’s not a coincidence that lately there have been many articles published about UX in the context of today’s hottest technologies, to encourage “innovative design thinking” methodology in the tech industry, research, and Innovation Labs. Designers are already leaving their comfort zones to make an impact everywhere, which is great!
Therefore, it’s very important for product designers to really understand the power of design-thinking, but it’s even more important to apply design-thinking in the tech industry, Innovation Labs and Startup ecosystems. Involve designers as early as possible, see things from different perspective, apply innovative design thinking alongside with engineering methodologies, because it’s important to understand that even if you are developing a disruptive technology, you must think about the end-user. Otherwise, it will be very difficult to figure out how to make your “disruptive” technology useful for the user.
Leave a Reply